He Tirohanga Hōmiromiro ki ā Mātau Mahi
Our Work in Detail
Intelligence Advantage
As New Zealand’s signals intelligence (SIGINT) agency, our role involves collecting and analysing electronic communications of significance to national security to produce intelligence. When appropriate, these products include intelligence sourced through our international partnerships.
We provide a range of intelligence products across all NSIPs under our function to contribute to the protection of New Zealand’s national security, international relationships, economic wellbeing, and the safety and security of New Zealanders.
Our legislation enables us to seek authorisation to intercept communications, seek assistance from telecommunications network operators and service providers, and receive intelligence from our international partners. Our legislation also permits us toaccess information infrastructures when authorised, allowing us to retrieve digital information directly from where it is stored or processed. We are subject to robust oversight, including from the Inspector-General of Intelligence and Security and Parliament’s Intelligence and Security Committee.
Regional Security and Geostrategic Competition
What happens in the Pacific has a fundamental impact on New Zealand’s own national security, prosperity and identity. We provide SIGINT in relation to New Zealand’s interests in the South Pacific. This focuses on providing support to other government agencies whose responsibilities include responding to security issues in the Pacific region.
Countering Foreign Interference
We work closely with the NZSIS and the wider national security system to understand how New Zealand’s people and sovereign structures are at risk from the foreign interference activities of other states. The NZSIS leads the NZIC’s efforts to identify and understand foreign interference activity by other governments.
Counter-terrorism
Our counter-terrorism effort has both a foreign and a domestic focus, and is aimed at ensuring New Zealand, New Zealanders, and our interests overseas are protected from extremism. Internationally, we continue to make a unique and highly valued contribution to global counter-terrorism efforts. This includes helping disrupt attack planning. Our work has focussed on formally designated terrorist entities and identity-motivated violent extremists. Violent extremist attacks worldwide continue to be inspired by online extremist rhetoric. The spread of extremist content and ideologies online remains a threat to New Zealand’s security.
Transnational Organised Crime
We are a participant in the New Zealand Police-led New Zealand Transnational Organised Crime (TNOC) Strategy. We provide intelligence and technical assistance to the New Zealand Customs Service (Customs) and Police to help counter TNOC.
The TNOC Strategy strongly aligns with the GCSB’s key objectives, which include contributing to the protection of New Zealand’s national security and wellbeing, and supporting the safety and security of New Zealanders at home and abroad.
Supporting NZDF
We contribute to NZDF efforts to detect and counter threats to New Zealand military personnel deployed overseas.
Customer Engagement
The Intelligence Customer Centre leads the provision of intelligence products to customers on behalf of the GCSB, NZSIS and DPMC. Our customers have a single point of contact and get the right information at the right time in a coordinated way. This is done through a range of activities, including in-person read services and digital read folders.
Sharing of Intelligence
The GCSB shares a significant amount of intelligence with foreign parties. This includes processing requests from Five Eyes partners to on-share GCSB intelligence with other parties. When the GCSB considers requests to share intelligence, we consider human rights risks alongside other considerations, such as whether the intelligence sharing may disclose intelligence sources or methods, or provide support to military operations.
The Pacific
Events of national significance in the Pacific have a fundamental impact on New Zealand’s own national security, prosperity and identity.
We and our Pacific neighbours exist in a security environment that is increasingly challenging for governments to navigate. The strong relationships New Zealand has with our Pacific neighbours are of great significance to us.
Security and resilience in the Pacific region has long been an important area of focus for New Zealand. The Pacific is increasingly an area of strategic competition for various great powers seeking to project influence into the region. This competition has a detrimental effect on regional security. Transnational organised crime also impacts the security of the region.
One of the Government’s National Security Intelligence Priorities is “Pacific resilience and security”, which focuses on understanding domestic and regional security issues in Pacific countries - those located in the New Zealand Realm, Polynesia, Melanesia, and Micronesia. This priority reflects the interconnectedness of the Pacific region and New Zealand’s security.
An increased number of countries compete for influence in the Pacific region through developmental funding, infrastructure builds, and proposals for military and security cooperation. This has national security implications for New Zealand.
Our role is to support wider New Zealand Government engagement with Pacific partners to enable a stable and prosperous Pacific region, for the protection of our shared fundamental values of democracy, human rights, and the rule of law.
The GCSB provides SIGINT in relation to New Zealand’s interests in the South Pacific. This focuses on providing support to other government agencies whose responsibilities include responding to security issues in the Pacific region.
We also work with our Pacific neighbours to improve cyber resilience. Our Pacific Partnerships team provides cyber security support and capacity building to Pacific Islands countries, building cyber resilience in the region.
The GCSB’s Role and Remit for Cyber Security
One of our core functions under the Intelligence and Security Act 2017 is to provide security advice and assistance, including conducting information assurance and cyber security activities. Our National Cyber Security Centre (NCSC) provides cyber security services to New Zealanders to support this remit.
We operate in a complex, challenging, and uncertain environment. Networks around the world remain vulnerable to malicious cyber activity. With mounting global reliance on complex shared systems for the delivery of services, malicious cyber actors seek new ways to infiltrate weak supply chain access points, and severely impact service delivery and information security.
We work to strengthen New Zealand’s cyber security resilience against these threats, helping our digital environment to withstand adversity. Our efforts to build cyber resilience include ongoing work across Government and critical infrastructure organisations to ensure the data and online services New Zealand relies on are protected against all hazards and risks. In addition, through our Director-General’s role as Government Chief Information Security Officer (GCISO), we provide system stewardship of information security for the public sector.
Following the integration of CERT NZ, we are also responsible for providing cyber security advice and education to all New Zealanders, offering support to New Zealanders who have been the target of malicious cyber activity, and for uplifting cyber security resilience in the Pacific.
Cyber threats are commonplace and becoming more complex. New technologies and threats continue to emerge, challenging existing cyber security practices. Incidents are having a larger impact on New Zealanders, causing economic and social harm. Cyber security is a core national security issue, as set out in the National Security Strategy. Together with DPMC, we are jointly responsible for leading New Zealand’s response to cyber security challenges.
Our cyber security remit is extensive – we are responsible for helping protect New Zealand from the most advanced cyber threats, while also providing support and advice to individual New Zealanders and New Zealand organisations when they are affected by cyber incidents.
We fulfil this remit through the following functional domains:
- We guide and govern cyber security decision making by developing standards, frameworks, policy advice, and governance.
- We identify and understand the New Zealand cyber security landscape to inform policy and operational decision-making.
- We prevent and protect New Zealand’s critical and classified information systems to reduce the potential impact of threats.
- We detect and contain malicious activity impacting New Zealand through our technical capabilities and partnerships.
- We respond and recover to reduce the impact of incidents by providing advice and incident response services across the whole economy.
The 2023/24 Year at a Glance
This was a year of significant change for the NCSC. We integrated with CERT NZ to become the lead operational cyber security agency for New Zealand, expanding our remit from nationally significant organisations and the public sector to include all New Zealanders.
Integrating CERT NZ with NCSC
In July 2023, Cabinet designated the GCSB as the lead government agency with whole-of-economy responsibility for cyber security operations. To give effect to this authority, the Government directed the transfer of CERT NZ from the Ministry of Business, Innovation and Employment to the GCSB. This transfer took place in August 2023.
In the immediate months after the transfer, CERT NZ remained a separate branch within the NCSC to ensure minimal disruption to staff and customers. Over the 2023/24 financial year, a new organisational structure was developed to more effectively align the two functions. We look ahead to the 2024/25 financial year with a merged organisational structure, upcoming co-location, and ongoing activity to align our products and services.
We continue to closely monitor the changing cyber landscape. As noted earlier, this year we recorded 7,122 incidents. Of these 6,779 were handled through our general triage process. Often these incidents impacted individuals or small to medium businesses. The other 343 incidents were triaged for more specialist technical support because of the nature of the victim, or the nature of the incident. These incidents have the potential to cause high impact at the national level.
Our annual Cyber Smart Week event took place in October 2023. This year, we created our ‘EXPOSED’ campaign, which told the real stories of 10 New Zealanders affected by cyber incidents. The week was successful, with over 1,200 businesses supporting the campaign, and 19,000 visits to the new Own Your Online website. Research showed that 70 percent of people who saw the campaign took action to be more secure online.
In March 2024, we called out malicious cyber activity targeting the Parliamentary Counsel Office and the Parliamentary Service. Our analysis of the tactics and techniques used by the actor enabled us to confidently link the actor to a PRC state-sponsored group known as APT40. We worked with the affected organisations to develop a comprehensive remediation plan, and joined partners in calling out these cyber actors.
This reporting year saw us undertake a review of our practices and procedures, to ensure we better consider the wider implications of cyber security incidents beyond our technical response. This review arose following phishing activity targeting members of the Inter-Parliamentary Alliance on China, where, although the malicious cyber activity was unsuccessful, the potential victims of the activity were not notified by the NCSC. The review showed there were aspects of our practice that could be improved and, at close of the reporting year, are working to implement the recommendations.
We also continued to advance our existing services and capabilities. This reporting year, our flagship Malware Free Networks® (MFN®) threat detection and disruption service achieved over 10 million disruptions since its launch in 2021. This is a significant increase from last year’s reported number of 390,000 disruptions, and reflects in part the uptake by partners including One NZ and Spark. MFN has helped New Zealanders avoid costly security incidents, and it makes a real difference to everyday New Zealanders’ lives. The positive impact MFN has had on New Zealand’s cyber threatscape received acclaim this reporting year, winning the 2023 Te Hāpai Hapori Spirit of Service Award for Service Excellence, as well as winning the overall Prime Minister’s Award.
The Threat Landscape
The GCSB continues to observe increasingly complex cyber threats from a growing number of sources, enabled by rapid advancements in technology, such as artificial intelligence, and the ever-increasing connectivity of devices and networks.
Malicious cyber actors are more agile in adapting to new technological environments, and they regularly change their methods in response to shifts in the cyber ecosystem. This includes the use of remote access operations, mass-exploitation of software vulnerabilities, supply chain compromises, and human-enabled cyber operations. Techniques, including sophisticated botnets and living off the land, continue to enable malicious cyber actors to evade detection and strengthen their ability to conduct successful computer network exploitation operations.
Globally, there has been a rise in the targeting of critical infrastructure. Government and critical infrastructure networks in New Zealand are almost certainly high-priority targets for both state-sponsored and financially motivated cyber criminals. State-sponsored actors likely intend to target these sectors for espionage activity, including the gathering of non-public government information, research data and intellectual property. Cyber criminals are attracted to these targets given disruption of important services may increase the chances of financial compensation. Operational technology connected to the internet and into corporate networks without proper controls also creates vulnerabilities for malicious cyber actors to breach these critical systems.
Cybercrime (such as ransomware) poses an immediate and widely experienced threat to New Zealand. Cyber-criminal activity is inherently opportunistic, but there is fast growth in its evolution owing to the worldwide industry of enablers, including access brokers and extortionists. Ransomware actors are increasingly taking advantage of exfiltrated data to extort payment from their victims, increasing the potential for reputational and economic harm, and impact to critical services.
State-sponsored cyber threat actors have also employed ransomware directly in their operations, both as a precursor to physical warfare and for profit. State-sponsored malicious cyber activity remains the most significant espionage threat to New Zealand organisations. New Zealand’s position in the world, including our international relations, involvement in global organisations, technological innovations and research is likely considered information of high intelligence value. State-sponsored cyber actors continue to demonstrate the intent and capability to target us for its acquisition.
Living off the Land
Living off the land refers to a technique used by malicious cyber actors to use tools already in their targeted environment to carry out an attack, rather than require the installation of scripts or codes within the target system. This can conceal the malicious cyber activity and make it harder for such attacks to be detected.
Cyber threat actors, including PRC and Russian state-sponsored actors, have been identified as using living off the land techniques in compromised critical infrastructure organisations. The US has observed indications of actors maintaining access and footholds for at least five years.
The NCSC joined international partners in publishing joint guidance in February 2024. The guidance provides information on common LOTL techniques and gaps in cyber defence capabilities.
Guide and Govern
We support New Zealand’s cyber security system by setting expectations about what good practice looks like through policies and standards, coordinating information sharing between organisations, and providing advice to the New Zealand Government on settings for critical infrastructure, cyber security procurement and communications security material.
Our work to Guide and Govern includes the GCISO system leadership role, providing strategic leadership as the authoritative Government voice on cyber security. Strong cyber security is a key enabler of productivity, economic growth, and the modernisation of public services.
We published version 3.7 of the New Zealand Information Security Manual (NZISM) in February 2024. The NZISM is a key part of our standards-setting role under the GCISO, establishing security expectations for agencies. This latest version of the NZISM includes technical guidance on cryptographic key management, embedding industry best-practice.
Work was also completed on an index to measure New Zealand’s ability to prepare for, respond to, and recover from cyber attacks. The Cyber Resilience Framework measures resilience in both consumer and business audiences and will help government agencies to track progress and improvements.
Reflecting the value of our partnerships with our Pacific neighbours, we work with Pacific states to help improve their cyber resilience. Our Pacific Partnership Programme (funded through the Ministry of Foreign Affairs and Trade) provides cyber security advice, training, and capacity building to Pacific Islands countries to help build cyber resilience. This programme supported the delivery of a Cyber Smart campaign to 15 partner countries, as well as cyber reporting tools, advisories, and technical training sessions.
In 2023/24, the Pacific Partnership Programme completed over 14 bilateral engagements and technical training sessions to both grow our understanding of Pacific nations’ cyber security needs and to develop cyber security skills across the Pacific, including taking part in the Samoa Cyber Roadshow. The team delivered multiple advisories and reporting tools to the Pacific, including the first Pacific Insights Report, and supported the delivery of a Pacific-specific cyber awareness campaign called ‘Cyber UP Pacific’ to 15 partner countries. In addition, we provided cyber security support to the Government of the Cook Islands when it hosted the Pacific Islands Forum meeting in 2023.
We also continue to work closely with our international partners on industry best practice and guidance. This reporting year, our products included the co-sealed guidance Guidelines for Secure AI, published alongside 23 agencies from 18 countries. This guidance helps organisations make informed secure decisions on the design, development, deployment, and operation of their AI systems.
Emerging Technologies
We continue to closely monitor the progress of emerging technologies, including artificial intelligence, and quantum computing.
We are interested in the potential AI has for supporting our work, as well as the national security risks it could pose. Like most organisations, the GCSB has been exploring AI’s potential benefits and developing our understanding of potential risks.
Regardless of the potential of AI to support our work, the legal safeguards and oversight arrangements we operate under will continue to apply. Like all disruptive technologies, the impact AI will have on our work and the operation of those safeguards is something we are taking time to understand fully. We are working with other government agencies on a framework for using AI in government and the wider economy.
Quantum computing is another advancement that offers opportunities and risks. The GCSB is working closely with our partners, and other international cyber security and standards bodies, to prepare for uptake in quantum computing. This includes providing new guidance to agencies through the NZISM on preparing for the impacts of quantum computing on information security controls, specifically related to encryption.
Identify and Understand
Part of our role is to identify, understand, and improve information security issues in the public sector. We work with agencies to monitor, measure, and analyse issues, and provide advice to mitigate vulnerabilities. The NCSC has unique insight and understanding of the cyber landscape and can use this to inform policy and operational decision making, aided by our GCISO function.
We also work to raise everyday New Zealanders’ awareness of cyber security issues, to help protect and improve individuals’ resilience to cyber threats. We do this through cyber security awareness campaigns, publishing quarterly reports about what is happening in the cyber threatscape, and providing advice and alerts to customers about how to respond to, and prevent, future attacks.
We publish alerts about high-priority vulnerabilities and provided them to our customers in order to support their decision making. This year we published 30 vulnerability alerts, 80 percent of which were published within 1 day of triage. We also co-seal advisory and attribution statements in conjunction with our international partners to raise awareness of cyber threats and provide information of value to cyber defenders to mitigate malicious cyber activity.
Working with our international partners is key to understanding the cyber security trends globally and how these may impact domestically. We participate in a range of international cyber security forums for sharing of information and best practice.
We continue to participate in the international CERT community through CERT-to-CERT engagements and contributions through forums. We contribute to these international groups with the goal of sharing our own expertise and supporting New Zealand’s own cyber resilience.
As cyber security is an area where the bulk of cyber security protections happen outside government, it is crucial we work with other sectors. To aid this, we facilitate information-sharing among organisations facing similar threats and challenges, especially where sharing requires a high level of trust. This primarily takes place through Security Information Exchanges focused on critical infrastructure. In the 2023/24 year, we co-chaired 24 Security Information Exchanges across the following six sectors: energy, finance, government, network-providers, universities, and transport and logistics.
We conduct technical attributions and analysis to identify those responsible for malicious cyber activity. These attributions are shared with domestic and foreign partners to inform understanding of cyber threats to New Zealand. While these are usually classified, the New Zealand Government can choose to publicly release the conclusions when it is in New Zealand’s interests to do so.
Case study: Parliamentary network breached by the PRC
In August 2021, the computer networks associated with New Zealand’s Parliamentary Counsel Office and the Parliamentary Service were comprised by malicious cyber actors. We attributed these malicious actors to a PRC group known as APT40. During the last three years, the PRC has demonstrated ongoing targeting of democratic institutions globally, and the targeting of critical infrastructure networks in the United States. We provided support against this attack.
This APT40 activity against Parliament was made public during the reporting year. Following the announcement, we joined partner agencies to highlight evolving tactics, techniques and procedures used by APT40. Its observed activity has included using compromised small-office/home-office devices as operational infrastructure, and exploiting newly public vulnerabilities in applications and devices.
By sharing this information publicly, we and other authoring agencies are raising awareness of, and resilience to, the tactics associated with significant cyber threats, to help protect and build resilience.
Prevent and Protect
We protect New Zealand’s information and prevent malicious cyber activity. We do this by maintaining New Zealand’s classified information and cryptographic systems, providing national security advice to inform regulatory decision-making on technology investment, and pre-emptively acting to disrupt threats to New Zealand. We also provide support to multi-agency events, such as the General Election and the Census.
Cryptographic Solutions and Development
Our Cryptographic Solutions and Development team ensures the New Zealand Government’s classified information systems mitigate emerging cryptographic and cyber threats. As New Zealand’s national authority for communications security, we build the maturity and capability of New Zealand by leading the cryptographic community towards fit-for-purpose, trusted and agile cryptographic solutions that conform to international standards.
We are currently developing a New Zealand cryptographic roadmap, which outlines the cryptographic modernisation initiatives being undertaken to ensure that classified information continues to be protected against emerging threats and known risks. The roadmap will help inform information owners and decision-makers, enabling owners of National Security Systems to plan for required upgrades and replacements for cryptographic solutions.
We continue to enable New Zealand Government agencies to protect their highly classified information through the operation of New Zealand’s Cryptographic Products Management Infrastructure (CPMI). CPMI is a secure ordering, generation, and distribution capability for encryption keys and other cryptographic services that handles the majority of encryption products provided by the GCSB. Through CPMI, we provide protection for a range of highly classified New Zealand Government communications, including emails sent by diplomats posted overseas, to air, land and sea communications systems deployed by the New Zealand Defence Force. We continue to support CPMI, including by maintenance, helpdesk and on-site support for client hosts.
Support to Major Events
The NCSC continues to provide cyber security support to major national events in coordination with crossgovernment efforts. The key events we provided cyber security support for in 2023/24 were the 2023 General Election, and the Pacific Islands Forum annual leaders’ meeting. Cyber security incidents could undermine the confidentiality, integrity or availability of data associated with an event, and events are likely of interest to both state-sponsored and criminal malicious cyber actors.
Regulatory Functions
We deliver regulatory functions under the following Acts:
- Telecommunications (Interception Capability and Security) Act 2013
- Outer Space and High-altitude Activities Act 2017
- Radiocommunications Act 1989, and
- Overseas Investment Amendment Act 2021.
The Telecommunications (Interception Capability and Security) Act 2013
Given its pervasiveness and comparative ease of access, telecommunications infrastructure is a highly attractive target for states seeking to engage in espionage, sabotage, or foreign interference, or for criminal actors looking to exploit New Zealand businesses and individuals. Network security has therefore become a key area of concern for preserving New Zealand’s national security, including its economic well-being.New Zealand’s telecommunications networks are a core part of critical national infrastructure. Organisations and individuals rely on network providers for safe and secure access to digital capabilities, and the secure provision of telecommunications services.
The purpose of the Telecommunications (Interception Capability and Security) Act 2013 (TICSA) in relation to network security is to prevent, mitigate, or remove security risks arising from the design, build, and operation of public telecommunications networks, or from the interconnection of public telecommunications networks to networks in New Zealand or overseas.
The TICSA established obligations for New Zealand’s telecommunications network operators regarding network security. The Director-General of the GCSB has a regulatory role for network security under Part 3 of TICSA.
Part 3 of TICSA also established a framework under which telecommunications network operators are required to engage with the GCSB about network changes or developments to their networks in areas of security interest. Many of these changes are currently driven by cloud adoption, increased demand for remote working, the rollout and expanded capacity of fibre optic cabling, and the transition to 5G services.
In 2023/24, the GCSB received 143 notifications network change proposals under TICSA.
Outer Space and High-altitude Activities Act 2017 and Radiocommunications Act 1989
We work closely with the NZSIS to conduct national security risk assessments for the growing space industry under the Outer Space and High-altitude Activities Act 2017, and Radiocommunications Act 1989. This national security risk assessment advice is used to inform Ministers, as required by the Act.
In the 2023/24 year, we conducted 21 assessments of regulated space activities under the Outer Space and High-altitude Activities Act 2017.
We conducted 74 assessments of regulated radio spectrum activities under the Radiocommunciations Act 1989.
Overseas Investment
Foreign direct investment is regulated by the Overseas Investment Office within Land Information New Zealand. Overseas investments are broadly considered to provide positive outcomes for New Zealand. However, foreign investment occasionally involves risks, including national security risks.
Both the GCSB and NZSIS support the Overseas Investment Office by providing national security advice on transactions which have been referred or notified under the Overseas Investment Amendment Act 2021. We work with the NZSIS to provide assurance to decision makers, as well as ensuring that investment into some of New Zealand’s most important and sensitive assets is done in a way that takes into account national security.
In the past year we provided advice to the Overseas Investment Office on 39 instances of proposals for overseas investment subject to the national security and public order notifications regime of the Overseas Investment Amendment Act 2021.
Detect and Contain
One of the NCSC’s core functions is to detect threats on New Zealand systems (where we have visibility), and to block these threats before they can cause an impact. We also issue critical alerts to potential victims that may be compromised, once we are made aware of vulnerabilities.
Cyber Defence Capabilities
Our cyber defence capabilities continue to improve security for New Zealand by protecting networks from malicious cyber activity. Through the provision of capabilities including the CORTEX suite of services and MFN, we ensure that organisations are less exposed to threats from malicious cyber actors. Our services are provided by express consent.
Collectively, these capabilities are provided to a subset of New Zealand’s central and local government, key research institutes, infrastructure providers, and key economic generators. These services are complementary to an organisation’s own security suite, and provide another layer of protection against malicious cyber activity affecting some of New Zealand’s most significant organisations. Our CORTEX suite of services prevented approximately NZ$38.8 million worth of harm to New Zealanders this year.
Our Phishing Disruption Service also extended its reach significantly during the year. Now, 85 percent of core public service agencies are benefiting from the service, which provides subscribers with high-quality phishing indicators they can block.
Technical Counter-Surveillance Unit
The NCSC’s Technical Counter-Surveillance Unit helps ensure New Zealand’s most sensitive communications are not intercepted or compromised. It provides technical security, emanations security, and accreditation services to ensure this information is not intercepted or compromised.
Technical security services are focused on countering technical surveillance techniques used by hostile actors, including eavesdropping and video surveillance. Emanations security services are focused on countering the threat posed by a spread of unintentional signals from ICT equipment that could be intercepted and interpreted by malicious actors. Our accreditation services check that highly classified information systems and sites are safe and secure for use.
Respond and Recover
We help New Zealanders to respond and recover once threats are found. The NCSC assists with incident responses, especially when incidents are of national significance.
Incident Response Services
Our Incident Coordination and Response function plays a vital role in safeguarding New Zealand’s nationally significant organisations against cyber threats that could impact New Zealanders’ national security and wellbeing. We triage incidents according to their potential national impact, engage with the victim to understand the scope of the activity, and support the victim throughout the incident’s lifecycle. This involves performing analysis and providing recommendations to support malicious activity containment, remediation, and recovery.
As significant incidents often require careful coordination of inter-agency, sector, and wider government actions, our responses often involve working closely with partners such as the New Zealand Police, and the private sector.
We recorded 6,779 incidents through our general triage process. Often these incidents affected individual New Zealanders and New Zealand businesses. Of these incidents, 99.6 percent were responded to within 4 working hours. Our quick response ensures that New Zealanders supported as soon as possible when an incident happens.
We continue to closely monitor the changing cyber landscape. As noted earlier, this year we recorded 7,122 incidents. Of these 6,779 were handled through our general triage process. Often these incidents impacted individuals or small to medium businesses. The other 343 incidents were triaged for more specialist technical support because of the nature of the victim, or the nature of the incident. These incidents have the potential to cause high impact at the national level trended upwards this year – from 316 in 2022/23 to 343 in 2023/24 - there has been a notable decline in the severity of the impact to New Zealand organisations.
This difference may reflect a number of contributing factors in the threat environment, including: recent disruptions to cyber-criminal infrastructure, changing state priorities or tactics, or the NCSC’s increasing ability to disrupt activity before harm takes place. Developments in our cyber defensive capabilities have allowed us to scale some services to a significant number of organisations, and even to home users.
Of the incidents we recorded 32 percent indicated links to suspected state-sponsored actors, compared to 28 percent in 2022/23. Nineteen percent were likely criminally or financially motivated. Although the total of criminal-linked incidents reduced by 19 percent in 2023/24, this reduction is likely to be temporary; there has been an upward trend in the first half of 2024, and we recorded a higher percentage of cyber-criminallinked incidents than incidents linked to state-sponsored actors for the first time in the previous financial year. This suggests the increasing volume of incidents from cybercrime is likely to continue in the coming years.
The remainder of incidents, 49 percent, were unattributed. These either represented preventative efforts undertaken by the GCSB before the activity could have a significant impact, or lacked the information needed to attribute the malicious activity.
In our triage process for specialist technical support we categorise incidents based on the severity of the compromise, as well as the significance of the victim organisation. The scale, from C1 being the most severe, to C6 being a minor incident, enables us to differentiate between a major and minor incident. This year’s most severe incidents were rated C3, with no C2 or C1 incidents recorded. Similar to the 2022/23 year, our most significant incidents were predominantly associated with ransomware or other extortion activity.
Supporting the National Security Sector
All-of-Government Data Centre
In addition to providing customers with signals intelligence and improving cyber resilience, we work to support
New Zealand’s National Security Sector to securely store sensitive information.
We partnered with the NZDF to construct an all-of-government data centre at Royal New Zealand Air Force Base Auckland (Whenuapai) to house New Zealand’s sensitive official information. As the government’s information security lead, we will operate the data centre on behalf of a range of government agencies.
Earth works commenced on the Whenuapai site in 2021, with construction beginning on the facility in September 2022. The data centre was publicly announced in April 2023 by the then Minister Responsible for the GCSB, Hon Andrew Little.
The data centre is expected to be operational by mid-2025, and will provide data storage for New Zealand government agencies for at least 25 years.
Ministerial Responsibility for the GCSB
As a public sector agency, the GCSB is politically neutral, providing impartial intelligence to our customers to enable their decision making. We also have a small policy function, which provides policy advice regarding issues of relevance to our portfolio.
When appropriate, we provide products, such as National Security Risk Assessments, to the Minister Responsible for the GCSB, to assist with their legislative responsibilities. The Minister, together with a Commissioner of Intelligence Warrants for activities in respect of New Zealanders, is the issuing authority for intelligence warrants that authorise GCSB activities that would otherwise be unlawful.
Given the joint enabling functions and similar focuses our agencies share, the Minister with portfolio responsibility for the GCSB is typically also the Minister Responsible for the NZSIS.
A General Election was held this reporting year. Prior to the election, our Minister was Hon Andrew Little. Following this, Hon Judith Collins KC was sworn in as the Minister Responsible for the GCSB in November 2023. The below measure reflects her assessment, as responsible Minister at the close of the reporting year.
Performance measure: Catalyse
Outcome: Minister trusts GCSB’s advice
| Assessment of Performance 2023/24 | Budget Standard | Actual | |||
|---|---|---|---|---|---|
| The Minister responsible for the GCSB receives best possible advice | |||||
| The Minister Responsible for the GCSB rates GCSB’s advice at least 3.5 (average) on a 5-point scale | At least 3.5 / 5 | 4.6 / 5 | |||
Our Sustainability Reporting
We continue to work towards meeting the requirements of the Carbon Neutral Government Programme (CNGP) and operating in an emissions and energy friendly manner.
Independent Verification
The GCSB completed independent emission verification for 2018/19 (our baseline year), and subsequent financial years.
The greenhouse gas emissions measurement (emissions data and calculations) reported in this annual report have been calculated in a variety of ways. These are based on solid supplier data, where it is available and practical, internal records, and an extrapolation of a sample of underlying financial records for certain emission sources.
In 2023/24 we estimate we emitted 2,350 Tonnes CO2-e, based on our sampled data and extrapolation. This compares to our verified figure of 2,244 Tonnes CO2-e in 2022/23. Most of our emissions came from passenger transport, as well as electricity and motor vehicles.
Our Reduction Targets
The Government set the following emission reduction targets for government departments, as required by the CNGP:
- 2025 target: Gross emissions (all Categories) to be no more than 1,875 Tonnes CO2-e, or a 21 percent reduction in gross emissions (all Categories) compared to the base year, and
- 2030 target: Gross emissions (all Categories) to be no more than 1,376 Tonnes CO2-e, or a 42 percent reduction in gross emissions (all Categories) compared to base year.
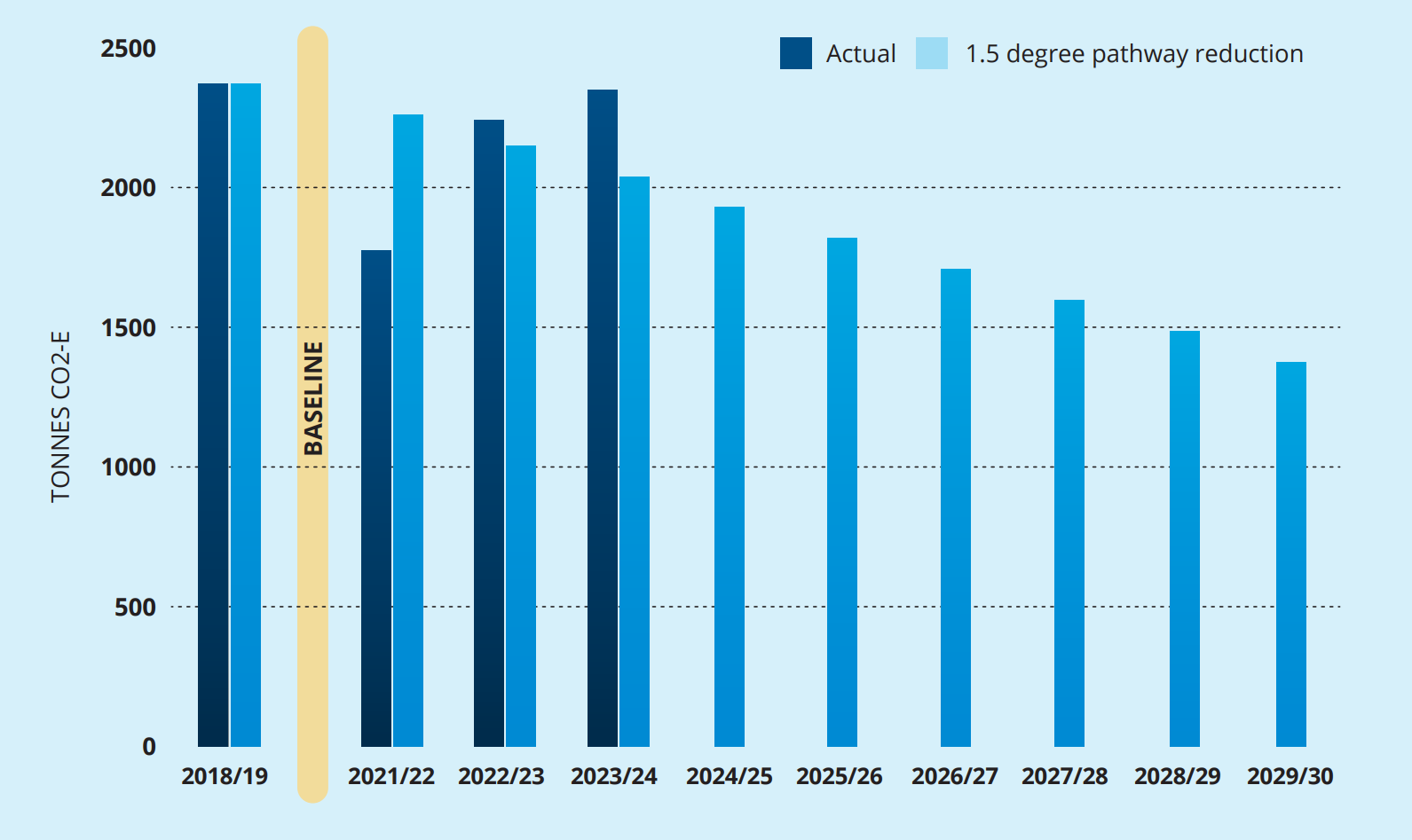
Chart: CO2-e GCSB Actuals vs 1.5 degree pathway reduction.
Accountability and Transparency
Te Noho Haepapa me te Pūataata Hoki
The Intelligence and Security Act 2017
The Intelligence and Security Act 2017 (ISA) provides the legal framework for the GCSB’s activities. The ISA sets out the objectives and functions of the GCSB and NZSIS, and provides the mechanism for us to carry out otherwise unlawful activities. There are 10 Ministerial Policy Statements relevant to the GCSB that set out Ministerial expectations and provide guidance on how certain lawful activities should be conducted.
The ISA requires periodic reviews of the GCSB, NZSIS and the ISA itself. Sir Terence Arnold KC and Matanuku Mahuika, with Dr Penelope Ridings as a special advisor, completed the first review on 31 January 2023. The resulting report, Taumaru: Protecting Aotearoa New Zealand as a free, open and democratic society, was made publicly available in May 2023.
The Government response to the ISA review is being jointly led by the Prime Minister and the Minister Responsible for the GCSB and NZSIS. DPMC administers the ISA and is the lead agency for responding to the review. We are working closely with DPMC to support the Government’s response.
Compliance Systems
An essential component of retaining the trust and confidence of the government and the public is having robust internal processes in place to ensure the GCSB complies with New Zealand law and our international human rights obligations at all times. The GCSB has a responsibility to ensure that we use our intrusive powers and access to sensitive information in a manner that is legal, justifiable and proportionate.
To ensure this, the GCSB has a compliance framework in place and audits operational activities. This provides assurance that staff are compliant with New Zealand law and that our compliance training and operational policies are fit-for-purpose, and support a strong compliance culture. Our policies are also reviewed in response to any relevant findings or recommendations made by the Inspector-General, or other Inquiries or independent oversight bodies.
Independent Oversight
The GCSB is subject to the oversight of several external bodies. Like other public sector agencies, this includes the Ombudsman, the Privacy Commissioner, Office of the Auditor-General, and Te Kawa Mataaho – the Public Service Commission. We are also subject to robust oversight from the Intelligence and Security Committee, and Office of the Inspector-General of Intelligence and Security.
The Intelligence and Security Committee
The Intelligence and Security Committee (ISC) is the Parliamentary oversight committee for the GCSB and NZSIS. The ISC’s role is to examine the policy, administration and expenditure of both agencies.
The ISC must have between five and seven members, comprising the Prime Minister, the Leader of the Opposition, and other members of Parliament nominated by the Prime Minister and the Leader of the Opposition.
Office of the Inspector-General of Intelligence and Security
The Inspector-General of Intelligence and Security (IGIS) provides independent external oversight and review of the GCSB and NZSIS. The IGIS provides assurance to the public of New Zealand that the activities of the GCSB are lawful and proper, which includes identifying any areas of concern.
The IGIS also provides an avenue for public complaints about the agencies’ conduct. The GCSB regularly engages with the Office of the IGIS to discuss issues and provide information and resources to support IGIS investigations and queries.
This reporting year, the IGIS published a report into the GCSB’s previous hosting of a foreign capability. While the report notes that at the time the GCSB undertook a reasonably robust investigation into the capability and the potential issues with hosting it, the GCSB accepts there were some failings in the decision-making processes that followed. The capability operated from 2013 until 2020, when the GCSB self-reported the capability to the IGIS.
As the IGIS report noted, our operations, governance, legal mandate, policies and compliance systems have changed significantly since the time the capability was operating. We are continually looking to improve how we work.
Statement of Warrants
In accordance with section 221(2) of the ISA, the following statements are provided for the period 1 July 2023 to 30 June 2024.
Co-operation
We did not provide any advice or assistance to the NZDF or the New Zealand Police for the purpose of exercising those agencies’ functions under section 13(1)(b). However, we co-operated with both agencies on a wide range of matters as part of performing the GCSB’s intelligence collection and analysis and protective security services, advice, and assistance (including information assurance and cyber security activities) functions. There were no occasions on which the GCSB provided assistance under section 14.
Intelligence Warrants
A total of 27 intelligence warrants were approved in 2023/24, of which 14 were Type 1 intelligence warrants and 13 were Type 2 intelligence warrants. No warrant applications were declined.
No applications for a joint intelligence warrant with the NZSIS were made under section 56. Joint intelligence warrants authorise the Directors-General of the GCSB and NZSIS to carry out the activities authorised by the warrant, and to exercise all of the powers of either agency to give effect to the warrant. While no occasion arose where the GCSB and NZSIS considered it necessary to seek such authority, the GCSB and NZSIS closely co-operate on operational matters.
Very Urgent Authorisations
(section 221(2)(1)(e) of the ISA)
There were no very urgent authorisations made by the Director-General under section 78. Very urgent authorisations are authorised by the Director-General where the delay in making an urgent application to a Commissioner of Intelligence Warrants and the Minister would defeat the purpose of obtaining the warrant. Such authorisations are automatically revoked 24 hours after the authorisation is given if an application for an intelligence warrant is not made.
Urgent Warrants
There were no applications for the urgent issue of an intelligence warrant sought under sections 71 or 72.
Restricted Information
No applications were made to access restricted information under section 136.
Business Records Directions
(section 221(2)(h) of the ISA)
A total of two business record approvals was applied for and issued. Two business records directions were issued by the GCSB to business agencies under section 150.
Performance Measure: Trusted
Outcome: Social licence from New Zealand’s public allows GCSB to operate effectively.
| Assessment of Performance 2023/24 | Budget Standard | Actual |
|---|---|---|
| Oversight agencies are confident in GCSB's legal compliance | ||
| The Inspector-General of Intelligence and Security (IGIS) rates GCSB's compliance performance at or above the well-developed level in at least four of the five headings in the IGIS Annual Report certification of compliance systems. | Achieved | Achieved |
| New Zealand public has trust and confidence in the GCSB | ||
| Public Service Commission Trust and Confidence survey Kiwis Count: Responses above 60 percent level for Q3B "Overall, to what extent do you trust the public service?". | Achieved | Not achieved1 |
1 At June 2024, Trust in the Public Service was reported at 56 percent. This figure reflects reported trust across all New Zealand public services.
Information Requests
The GCSB is subject to the Official Information Act 1982 (OIA) and the Privacy Act 2020. We aim to be as transparent as possible in responding to requests made under these Acts while safeguarding important matters such as the security or defence of New Zealand. Each request is assessed individually, and matters such as national security concerns are considered within the guiding statutory principles. The GCSB aims to complete all information requests within the legislated timeframe. Due to the joint enabling functions we share with the NZSIS, we provide combined OIA responses when appropriate with the NZSIS.
| 2019/20 | 2020/21 | 2021/22 | 2022/23 | 2023/24 | |
|---|---|---|---|---|---|
| OIA | 51 | 49 | 70 | 59 | 75 |
| PA | 28 | 27 | 16 | 23 | 19 |
The median response time was 16 working days across all OIA and Privacy Act requests. This compares to 19 working days in the previous reporting year. All requests were responded to within the legislated timeframe.
The Office of the Ombudsman and the Office of the Privacy Commissioner provide important oversight of the GCSB’s activities.
The GCSB was notified of three complaints by the Office of the Ombudsman during the reporting period. One complaint was resolved with the Ombudsman finding in the GCSB’s favour; one found against the GCSB. The third complaint remained under consideration at the close of the reporting period.
The GCSB was notified of two complaints by the Office of the Privacy Commissioner during this period. Both were resolved to the satisfaction of the Office of the Privacy Commissioner, which found the GCSB had not breached the complainant’s privacy.
Performance Measure: Trusted
Outcome: Social licence from New Zealand’s public allows GCSB to operate effectively.
| Assessment of Performance 2023/24 | Budget Standard | Actual |
|---|---|---|
| GCSB meets its legal obligations: Official Information Act 1982 | ||
| 100 percent of OIA requests are completed within the legislated timeframe | Achieved | Achieved |
| More than 50 percent of final opinions formed by the Ombudsman are found in favour of GCSB | Achieved | Achieved |
| GCSB meets its legal obligations: Privacy Act 2020 | ||
| 100 percent of Privacy Act requests are completed within the legislated timeframe | Achieved | Achieved |
| More than 50 percent of investigations by the Office of the Privacy Commissioner found that GCSB did not breach the Privacy Act and cause the complainant harm | Achieved | Achieved |
| New Zealand media and commentators are well informed about the GCSB | ||
| Assessment by the GCSB communications team about the accuracy of media reporting about the GCSB | Achieved | Partially achieved2 |
2 We continue to work to improve media and commentators’ understanding of the GCSB’s roles and functions.
